今天要來說一下 Etherchannel 的 Port-channel 配置
這個是很好用的一项技術應用呢! 實在深感我心
這裡要先提到PAgP 與 LACP這兩種協定:
PAgP : 是Cisco 私有的協定,每30秒數據會發送一次進行偵測
適用範圍: Cisco device to Cisco device
mode:
Auto : 這種模式會使端口進入被動協商,對PagP數據包有反應但不會發起主動協商
Desirable : 這種模式會使端口進入主動協商。接口會透過發送PAgP來與其他接口進行協商
On: 不使用PAgP來形成Enterchannel
Non-silent: 如果交換機連接到有PAgP能力的設備,可以將接口配置為non silent。non silent為auto或desirable模式指定non-silent關鍵字,如果沒指定就會假設狀態為silent。而silent
。沉默設置被用於連接到文件服務器或包分析儀。該設置允許PAgP,將接口添加至Channel組,並使用接口進行傳輸
LACP: 是IEEE的開放協定的一部分 (802.3ad)
適用範圍: Cisco device to Cisco device
Cisco device to other device
other device to other device
mode:
Passive:會進入被動協商狀態,端口會對LACP數據包做出回應,但端口不會主動發起協商
Active:會進入主動協商狀態,端口會通過發送LCAP數據包來主動與其他接口進行協商
On: 強制形成EtherChannel ,並且不需要使用PAgP或LACP進行協商
範例:
CS1 是一台L3的Switch , ES1 L2的Switch
老闆說因為沒錢買10GB Lan的Switch ,但ES1的流量實在太大, 要不你自己想辦法改一改吧....讓Switch與Switch之間的水管通道大一點...越大越好 越大越好 越大越好
小麥克: 阿是要多大....OOXX
CS1: gi0/1 - gi0/2 Port
ES1: gi1/1- gi1/2 Port
做法如下:
=================================================================
1. 關閉CS1 gi0/1 - gi0/2 Port與ES1的 gi1/1 - gi1/2 Port
CS1設定
CS1(config)#int range gi0/1-2
CS1(config-if-range)#sh
CS1(config)#int port-channel 1
CS1(config-if)#switchport trunk encapsulation dot1q
CS1(config-if)#switchport mode trunk
CS1(config-if)#exit
CS1(config)#int range gi0/1-2
CS1(config-if-range)#switchport mode trunk
CS1(config-if-range)#channel-group 1 mode ?
active Enable LACP unconditionally
auto Enable PAgP only if a PAgP device is detected
desirable Enable PAgP unconditionally
on Enable Etherchannel only
passive Enable LACP only if a LACP device is detected
CS1(config-if-range)#channel-group 1 mode on
%LINK-5-CHANGED: Interface Port-channel 1, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface Port-channel 1, changed state state to up
ES1設定
ES1(config)# int range gi1/1-2
ES1(config-if-range)#shutdown
ES1(config)#int port-channel 1
ES1(config-if)#switchport mode trunk
ES1(config)#int range gi1/1-2
ES1(config-if-range)#switchport mode trunk
ES1(config-if-range)#channel-group 1 mode on
%LINK-5-CHANGED: Interface Port-channel 1, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface Port-channel 1, changed state to up
CS1與ES1檢查方式相同:
檢查1:
CS1#show interfaces etherchannel <<檢查一下所有etherchannel的狀態如何
GigabitEthernet0/1:
Port state
= 1
Channel group
= 1 Mode = On Gcchange = -
Port-channel = Po1 GC = - Pseudo port-channel = Po1
Port index = 0 Load = 0x0 Protocol = -
Age of the port in the current state: 00d:00h:06m:18s
GigabitEthernet0/2:
Port state
= 1
Channel group
= 1 Mode = On Gcchange = -
Port-channel = Po1 GC = - Pseudo port-channel = Po1
Port index = 0 Load = 0x0 Protocol = -
Age of the port in the current state: 00d:00h:06m:18s
----
Port-channel1:Port-channel1
Age of the Port-channel = 00d:00h:20m:15s
Logical slot/port = 2/1 Number of ports = 2
GC = 0x00000000 HotStandBy port = null
Port state =
Protocol = 3
Port Security = Disabled
Ports in the Port-channel:
Index Load Port EC state No of bits
------+------+------+------------------+-----------
0 00 Gig0/1 On 0
0 00 Gig0/2 On 0
Time since last port bundled: 00d:00h:06m:18s Gig0/2
檢查2:
CS1#show etherchannel port-channel << 看一下etherchannel下的port-channel狀態
Channel-group listing:
----------------------
Group: 1
----------
Port-channels in the group:
---------------------------
Port-channel: Po1
------------
Age of the Port-channel = 00d:00h:29m:23s
Logical slot/port = 2/1 Number of ports = 2
GC = 0x00000000 HotStandBy port = null
Port state = Port-channel
Protocol = PAGP
Port Security = Disabled
Ports in the Port-channel:
Index Load Port EC state No of bits
------+------+------+------------------+-----------
0 00 Gig0/1 On 0
0 00 Gig0/2 On 0
Time since last port bundled: 00d:00h:15m:26s Gig0/2
檢查3:
CS1#show ip interfaces brief <<看一下state and protocol是否都upup
Interface IP-Address OK? Method Status Protocol
~中間省略~
Port-channel 1 unassigned YES unset up up
檢查4:
CS1#show interfaces trunk <<檢查一下Port-channel的 trunk是否正常
Port Mode Encapsulation Status Native vlan
Gig0/1 on 802.1q trunking 1
Gig0/2 on 802.1q trunking 1
Po1 on 802.1q trunking 1
Port Vlans allowed on trunk
Gig0/1 1-1005
Gig0/2 1-1005
Po1 1-1005
Port Vlans allowed and active in management domain
Gig0/1 1
Gig0/2 1
Po1 1
Port Vlans in spanning tree forwarding state and not pruned
Gig0/1 1
Gig0/2 1
Po1 1
檢查5:
CS1#show interfaces <<看一下Pore-channel1的介面詳細資訊
Port-channel 1 is up, line protocol is up (connected)
Hardware is Lance, address is 0010.1167.4c4a (bia 0010.1167.4c4a)
MTU 1500 bytes,
BW 2100000 Kbit, DLY 1000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Half-duplex, 2100Mb/s
input flow-control is off, output flow-control is off
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:08, output 00:00:05, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue :0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
956 packets input, 193351 bytes, 0 no buffer
Received 956 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
0 watchdog, 0 multicast, 0 pause input
0 input packets with dribble condition detected
2357 packets output, 263570 bytes, 0 underruns
0 output errors, 0 collisions, 10 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier
0 output buffer failures, 0 output buffers swapped out
這樣完成
Port-channel 的設定了~ 幹的好阿小麥克
接下來...我們來實驗一下...斷掉其中一個Prot-group 的Port 會發生甚麼事
下圖接上兩台PC
PC-A:192.1680.1
PC-B: 192.168.0.2
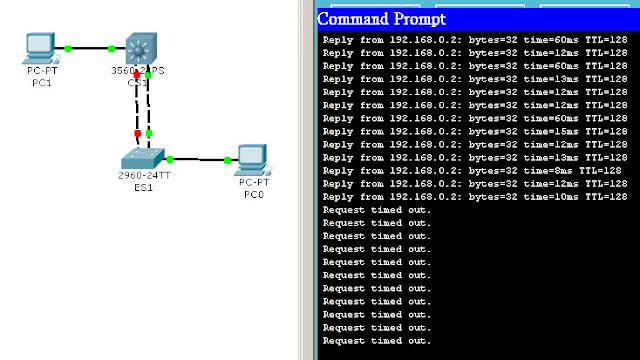
讓PC-A不斷的ping PC-B 看起來都很正常
從ES1中showdown gi1/1 假裝這條線失憶了XD..沒想到這port-channel就掛掉了
所以說....有一好沒兩好...要解決這問題我看在建兩組Port-channel然後再做STP或RSTP就可解決增加頻寬也有備援,缺點當然是損失的Port會比較多一點
疑難排解:
=================================================================
目前建置都很順...我也不知道該產生出甚麼問題,有遇到問題
=================================================================
當然, 如果您有更好的方法,也請與我交流.....因為我只是菜鳥一個